Managed Security Services
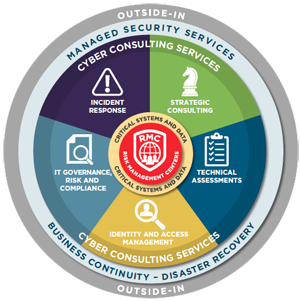
Managed Security Services (MSS) is a systematic approach to manage an organization's security needs. Odessa Advisors as an MSSP provides this service in both ways, in-premise as well as remote-management to oversees company’s network and information system security. This diverts the burden of performing the chores manually, which can be considerable, away from administrators.





