Application Whitelisting & Control Management
- last line of defense
Over 30 million new malware signatures (as per CNN) are now identified each month.
More sophisticated and zero-day attacks are also on the rise.
And traditional, single line-of-defense security tools such as anti-virus are not able to keep up.
In an Enterprise, it is essential that computer users get only the applications they require to be productive and are unable to access or introduce unauthorized applications which reduces desktop stability, impacts security, breach licensing compliance, lead to user downtime and increase desktop management costs.
This scenario impacts organizations' bottom line significantly - malware driven costs can be as much as 50 percent of an organization's endpoint TCO due to increased help desk calls, reimaging costs, network downtime and lost employee productivity.
The Solution

Application Whitelisting & Control Management is the only pro-active next-generation tool which provides effective malware protection and increases IT and end-user productivity by preventing any zero-day (unknown), un-trusted, malicious or unauthorized applications from executing as well as managing authorized application library.

Guilt Until Proven Innocent
For AWCM, any application is treated as a threat till it is not proven clean. Thus, AWCM enables an enterprise to prevent from attack by any known or unknown malware or Ransomware. It blocks unknown malware that bypasses all other defenses. It doesn’t matter whether it came from a website or a USB or other way. It doesn’t matter that it was an executable, a self-extracting file, a script, a registry key or a screen saver.
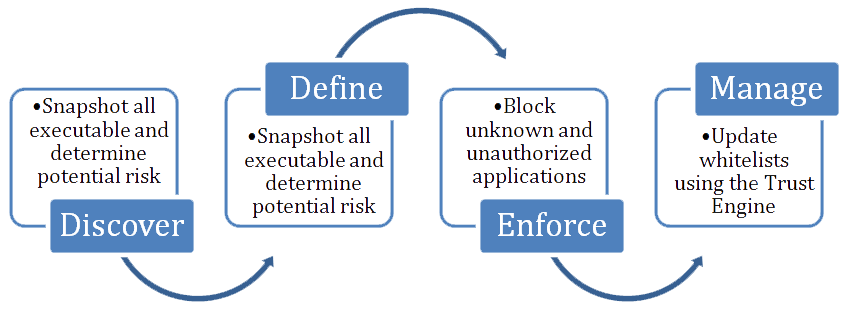
With AWCM, IT administrators can quickly identify all applications running in their environment and enforce a comprehensive whitelist policy that prevents unauthorized applications, malware and un-trusted change. Application access entitlements can be defined on endpoints. Only trusted applications installed or permitted by administrators are allowed to execute, while any user-introduced applications and even unknown code is automatically prevented from launching by default.
How AWCM Works?
Features & Benefits
Features |
Benefits |
| - Application Whitelisting | - Desktops remain in original gold-built state |
| - Advanced Memory Protection | - Prevent unknown applications or malicious code from executing |
| - Application Reputation Scoring | - Increased system uptime, security and user productivity |
| - Easy Auditor / Lockdown | - Reduce the threat of unknown malware & Ransomware |
| - Automated Trust Engine | - Forensic Trail of attempts to breach security |
| - Local Authorization | - Provides Continuous Application Visibility and Control |
| - Centralized Application Management | - Prevents Targeted Malware and Zero-Day Attacks |
| - Application Event Log | - Protects Against Memory Injection Attacks |
| - Denied Application Policy | - Enforces Trusted Application Environment |
| - Flexible User- and Machine based Policy Enforcement | - Improves System Performance and Availability - Reduces Endpoint Security TCO |
| - Offline Computer Protection | - Integrates with Antivirus, Device/Port Control and Patch Management Tools for Defense-in-Depth |
The Impact and Savings
Based on extensive customer feedback, it may take some organizations on average 2 days to fully lockdown a corporate application, including finding all associated code, locking down the application, thoroughly testing lockdown configurations, and finally deploying the configuration. According to Gartner, the number of applications in the average organization represents approximately 10% of the number employees in the organization. AWCM replaces this time consuming and costly exercise by using out-of-the-box technology to automatically control application access at just a fraction of the cost without high maintenance lists or complex scripts.